Remove Gfi Endpointsecurity Agent Service
- Posted in:Admin
- 16/12/17
- 72

GFI EndPointSecurity. How to manually remove a GFI LanGuard Agent. The main application already indicates the agent is not installed but the service.
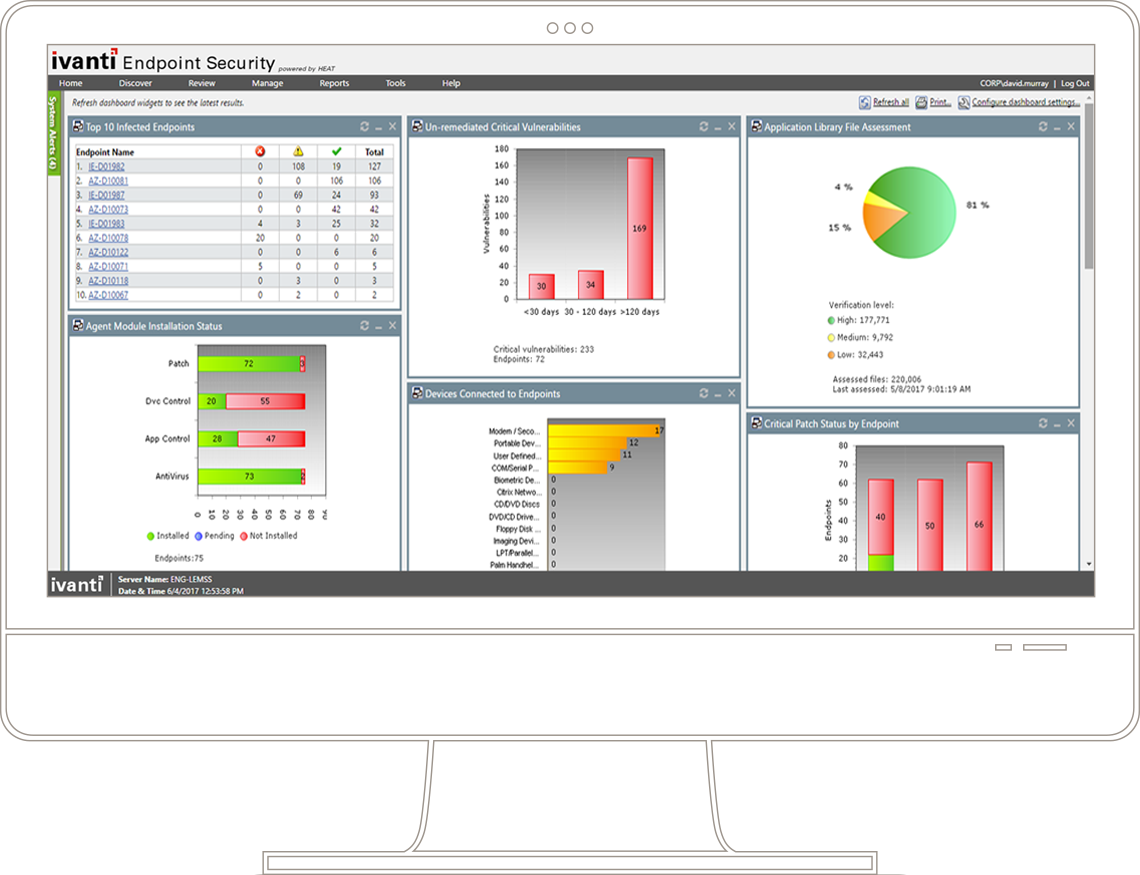
Overview: Comprehensive control on use of iPods, USB sticks and other portable devices The proliferation of consumer devices such as iPods, USB sticks, smartphones and other portable devices has increased the risk of data leakage and malicious activity on networks. While most companies have antivirus, firewalls, and email and web content security to protect against external threats, few realize how easy it is for an employee to copy huge amounts of confidential and commercially-sensitive data onto an iPod or USB stick without anybody knowing. There is also a high risk of viruses, malware and illegal software being introduced on the network. A draconian way to prevent this from happening is to lock down all USB ports, but this is neither sustainable nor feasible. Prevent the risk of data leakage Bring your own device (BYOD) and portable storage device use in the workplace significantly increase the likelihood of your business facing data leakage issues. Brick Lace Love Is Wicked Mp3 Download Free.
GFI EndPointSecurity features risk assessment capabilities that identify assets possibly doubling as sources of data leaks. All functionality is built into a dashboard that provides relevant information, suggestions for boosting protection, and shortcuts to common security tasks. Assess and control information that travels across endpoints The data awareness module provides another layer of endpoint protection by scanning each relevant file and searching for the most common types of information susceptible to a security breach (e.g.
SSNs, PANs, etc.). The module supports inputs in the form of regular expressions and dictionary files. It also contributes to your data loss prevention (DLP) and compliance efforts. Easily control access to portable storage devices From a single location, easily grant temporary network or workstation access to portable storage devices for a set period of time as well as block devices by class, file extension, physical port or device ID. Protect your network GFI EndPointSecurity helps prevent the introduction of viruses, malware and other unauthorized software to your network by blocking access to a wide variety of devices such as USB sticks, iPods and smartphones. Control access Prevent data leaks by comprehensively controlling access to portable storage devices with minimal administrative effort. Temporary access can be granted to users for a device (or group of devices) on a particular computer for a particular timeframe.
Encrypt removable devices GFI EndPointSecurity can be set up to enforce encryption on removable USB storage devices. Prevent data theft Most data theft happens by employees manually transferring it onto devices. Controlling access to computers helps you prevent this. Take control of your network You can block devices by class, file extensions, physical port or device ID from a single location, while granting temporary device or port access for a stipulated timeframe. Centralize monitoring View all computers on your network from a single location, and benefit from GFI EndPointSecurity’s detection of connected devices and its ability to perform tasks. Automatic protection Automatically protects newly detected computers by deploying an agent and a default blocking policy. Generates detailed reports Logs detailed statistics about all activity and can send automatic daily or weekly digests.
Control portable device access to your network with GFI EndPointSecurity GFI EndPointSecurity enables administrators to actively manage user access and log the activity of: • Media players, including iPods, Creative Zen and others • USB drives, CompactFlash, memory cards, CDs, floppies andother portable storage devices • iPhone, BlackBerry and Android handhelds, mobile phones, smartphones and similar communication devices • Network cards, laptops and other network connections. GFI EndPointSecurity QuickVid. What's new in GFI EndPointSecurity 2013 SR1? AES-256 encryption The volume encryption feature of GFI EndPointSecurity now offers AES-256 along with the already existing AES-128. Permissions for specific device serial numbers A policy can contain now permissions for specific device serial numbers which are very useful in cases when a specific device having a unique serial number has to be treated differently.
Risk Scanning of Windows 8 and Windows Server 2012 machines GFI EndPointSecurity adapted to the technology change in the two new operating systems offering now the full scanning functionality for them. Improved agent protection The GFI EndPointSecurity agent protection was improved to block users trying to tamper with the agent and gain access to devices.